Security and Privacy Assessment
We help you eliminate hidden source code weaknesses to protect the security of your data and the privacy of your customers.
Let’s Talk59%

increase in reported security flaws
new CVEs were reported in 2022

Eliminate Weaknesses
Ensure the right security and privacy controls are built into your IT

At SIG, we combine our consultants' expertise with the leading tooling of our Sigrid® platform to help you ensure the security of your data and the privacy of your customers. Our solution provides:
Benefits

Prioritized actions without a flood of violations
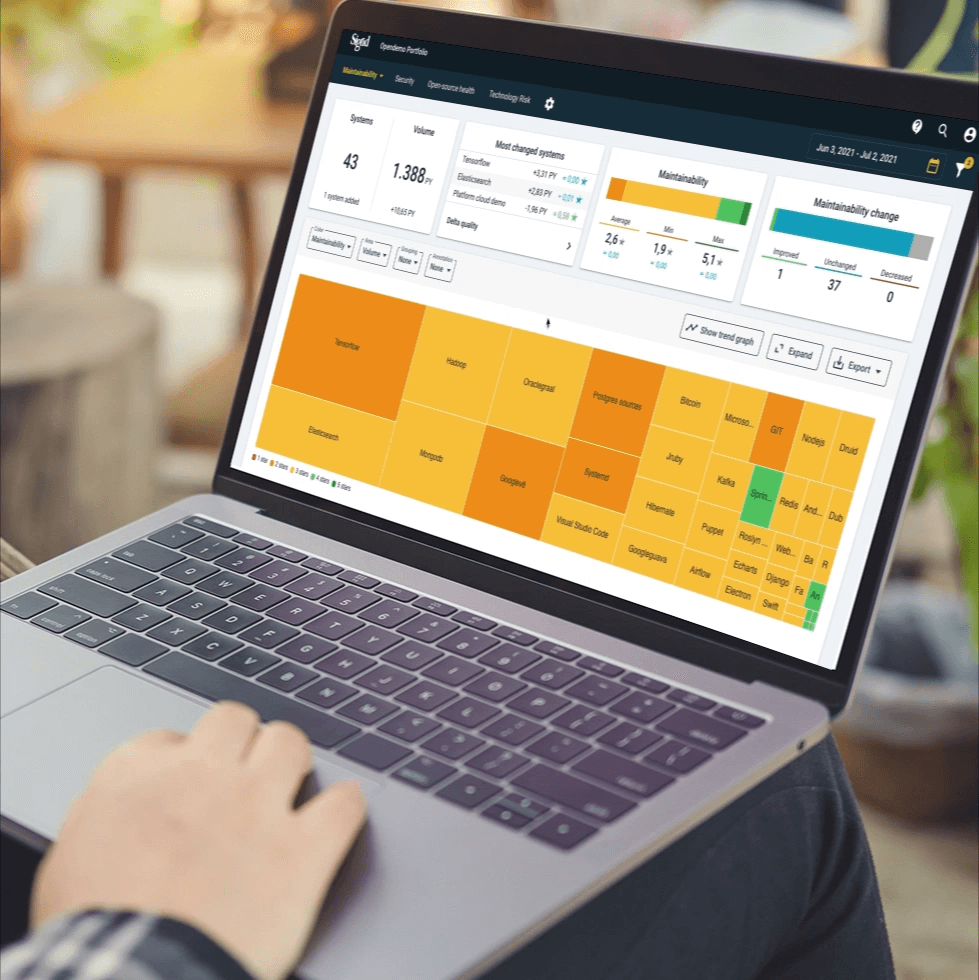
Sigrid® provides you with a prioritized list of clear actions, not a firehose of findings overloading your developers.

Insight from bit to boardroom
Sigrid® provides high-level portfolio overviews of code-level violations as well as deep-dive findings around aspects such as system architecture. Whether it's the CIO or the last developer, all stakeholders get the appropriate insight.

Analysis from the inside out
A full security audit requires an assessment beginning with the code itself. Our consultants, with the help of our leading tooling, will analyze the source code and identify and prioritize findings.

Vulnerability Scanner
Sigrid performs a full security analysis on source code, identifying and prioritizing issues. Our consultants then translate these findings into recommended actions.
Our Clients.
Who we help