
24 July 2024
Request your demo of the Sigrid® | Software Assurance Platform:
5 min read
Written by: Nick Potts

Software Bill of Materials (SBOM) is rising to the top of IT priorities, especially within U.S. government agencies. President Biden issued Executive Order 14028 to address “persistent and increasingly sophisticated malicious cyber campaigns.” The White House details in section 4 that the security of the software supply chain needs to be enhanced to resist attack and prevent tampering.
The idea of pulling together a list of third-party open-source packages should be a straightforward process. The reality is more complex as modern software is usually dependent upon multiple packages that may be dependent on other packages, and so on, and so on.
Any SBOM report should follow a standardized format detailing the packages and every modification. The report should be automated, making it easier to track changes as software is maintained, upgraded, or new packages are added/removed. This living document strengthens business resilience as it proactively highlights vulnerabilities and helps improve software security.
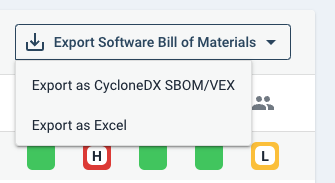
The Cyclone DX Software Bill of Materials (SBOM) is a complete and accurate inventory of all third-party components. This standard exceeds the minimum SBOM requirements, as defined by the National Telecommunications and Information Administration (NTIA) in response to U.S. Executive Order 14028.
In addition, Sigrid® | Software Assurance platform embeds the Vulnerability Exploitability Exchange (VEX) information within the SBOM. This convenience creates a single file that contains the latest vulnerability details, exploitability, and detailed analysis associated with each open-source package. Clients can quickly locate known vulnerabilities and take action to remediate a fix.
When new vulnerabilities are discovered and publicly reported, these security findings are automatically included in subsequent exports.
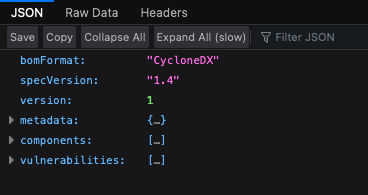
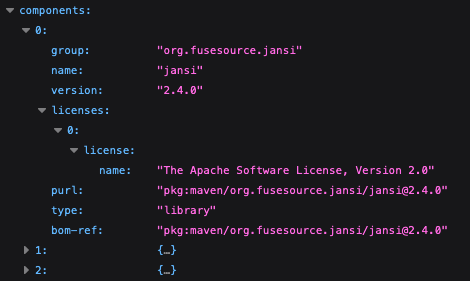
Below is a screenshot of the SBOM with the different parts minimized. At the very top is the SBOM Format, the specific version, and the version.
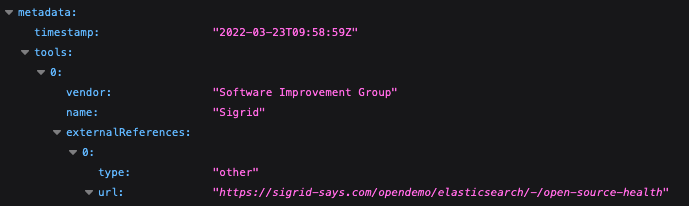
Within the Metadata section, the following fields are provided: timestamp, tools including vendor and name, and external references including type and URL.
Within Components, for each item, the group, name, version, and licenses are listed including the name, purl, type, and BOM reference.
Within vulnerabilities for each item, the BOM reference and the vulnerability identification (CVE), severity score and categorization, method, and vulnerability description.
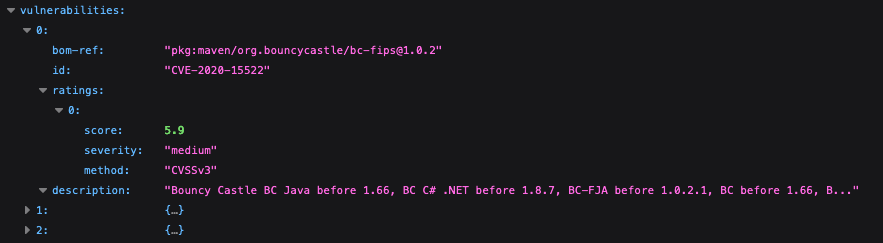
SBOM Vulnerabilities details
Sigrid® | Software Assurance platform helps clients easily generate SBOMs that enhance business resilience and strengthen software security. Integrate Sigrid® fact-based findings into your software development lifecycle to improve the quality and security of your software.
Want to see how quick it takes to generate an SBOM? Contact us and we’d be happy to show you how we help our clients mitigate risks regarding their software supply chains.
Author:
Growth Marketing Manager

We'll keep you posted on the latest news, events, and publications.