system inspections

Actionable findings
Are you going to hit your strategic objectives?

+200B
Lines of Code
In 60 minutes, the Sigrid | Landscape Scan gives you an overview of the real-life status of your application landscape, indicating your top Security and Open-source health risks along with actionable recommendations on:
Code Quality
Security Prioritization
Test Code Analysis
Open-Source Risks
Technical And Architecture Debt
With Sigrid | Landscape Scan, start working on clearly identified vulnerabilities and confidently execute your business plan.
Our high-level report will be presented to you by a delivery director in a 1-to-1 meeting. It gives you clear visibility on the health of your applications, hidden risks in 3rd party libraries & security vulnerabilities, as well as actionable recommendations for managing Technical & Architecture Debt.
Valuable
The landscape scan gives insights into the reality of your landscape so you can prioritize planning & budgeting based on the factual status of health and risks
Fast
We scan up to 1,000+ systems in one day per customer
Tangible deliverables
In one week, you will receive your Sigrid® | Landscape Scan report with the high-level findings and a management presentation
Monitoring progress
The scan is a stepping stone to actively monitoring the progress of your most critical systems
Easy to use
The results are intuitive and actionable
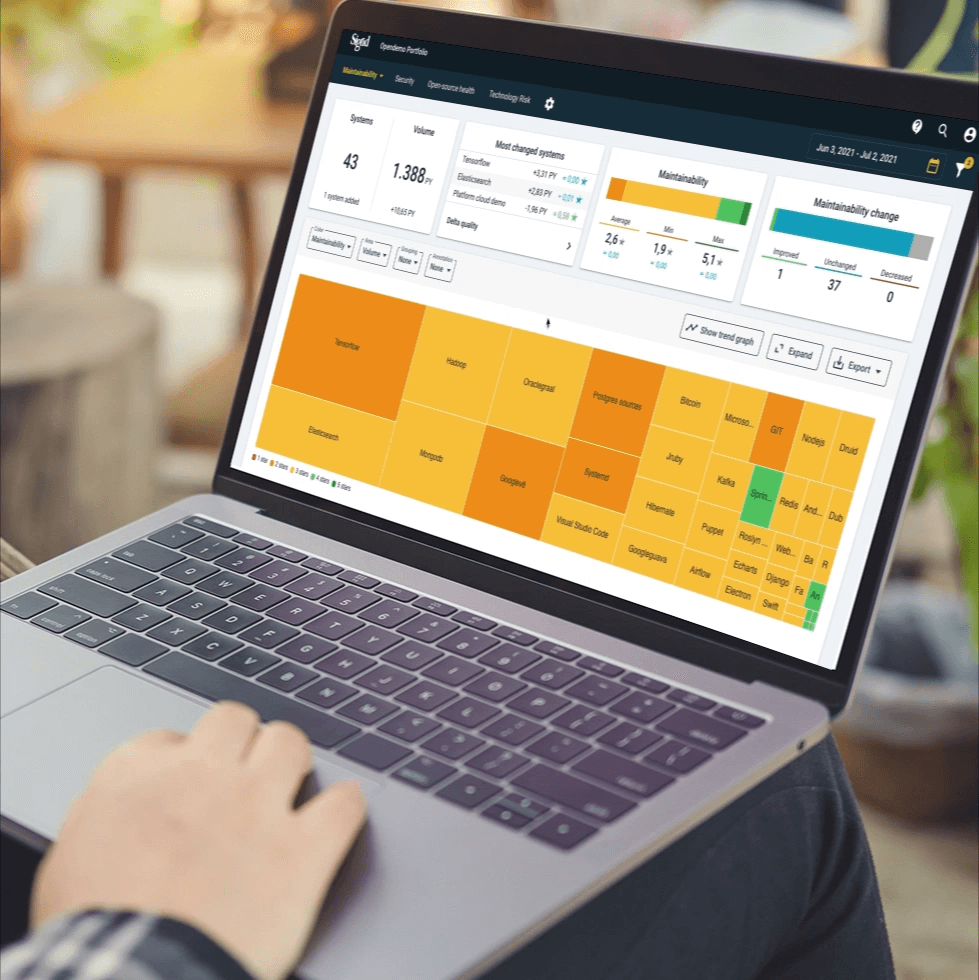
Sigrid | Landscape scan - Sample results
01/02
Portfolio Summary
The overall health of your portfolio scores low. A high amount of technical debt and security findings make the business vulnerable and less adaptable to changing customer needs.
Request a sample report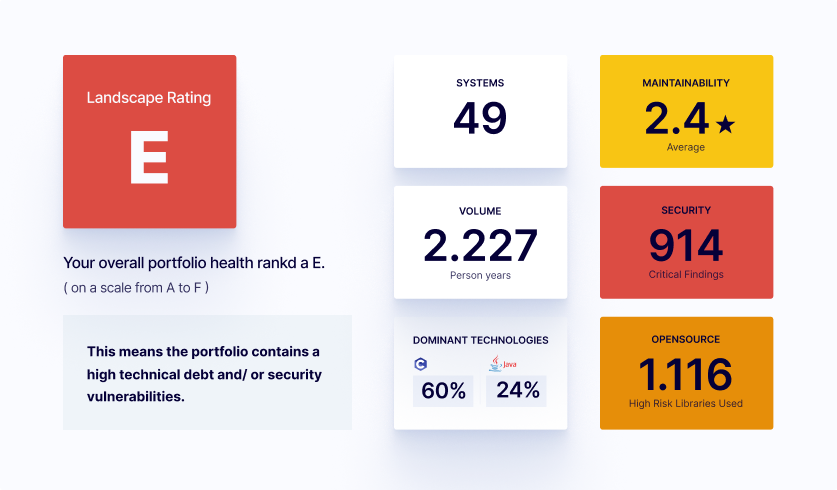
02/02
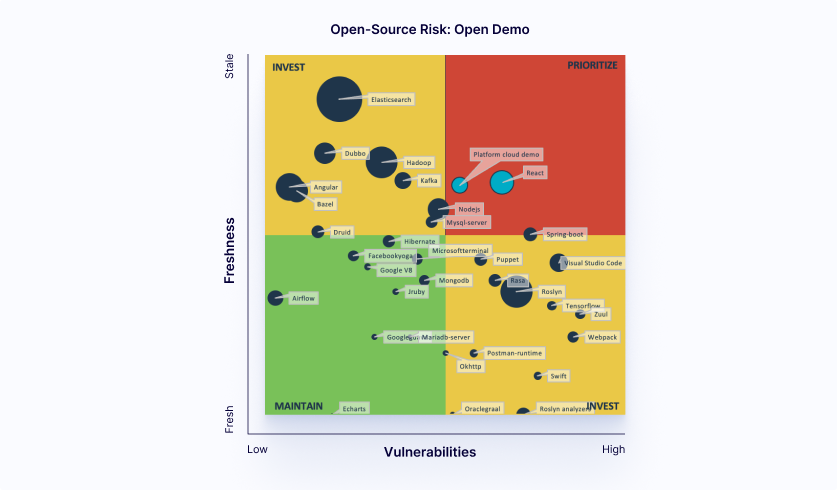
Security prioritization
A large number of smaller systems are easier to change but contain critical vulnerabilities. Systems like Puppet and Webpack have above-average code quality but contain vulnerabilities.
Our Recommendations
Investigate the security risks of all systems in the two right-hand-side quadrants, utilize our findings to prioritize fixes and implement a remediation plan.
Where possible, start solving these issues in the ‘Invest’ quadrant. These systems have serious issues that should be easier to change.
+200B
Lines of code