Software quality management and cybersecurity
In this article
From day-to-day processes to mission-critical operations, software is a necessary part of running a business, and for many, it is the business itself.
Despite our increasing reliance on software, its quality – extending beyond mere functionality – often takes a back seat.
This oversight can lead to more issues than you might think: financial losses, operational disruptions, reputational damage, and more.
In 2024, data breaches cost businesses an average of USD 4.88 million, In Europe, more than 10 terabytes of data is stolen monthly, and a whopping 32% of UK businesses have experienced a cyber breach or attack in the last year alone.
These figures highlight the urgent need for technology leaders to prioritize software quality and implement secure coding practices to reduce risk.
At Software Improvement Group, we’ve established that there is a direct relationship between the build quality of software and the emergence of vulnerabilities.
By deeply ingraining software quality throughout the entire software development lifecycle (SDLC), you can not only detect vulnerabilities early but also better defend your business against such threats.
This article will explore the impact that threats, vulnerabilities, and risks have. We’ll discuss how high-quality software acts as a preventive measure against these issues, the advantages it brings, and offer some straightforward strategies to ensure you’ll make your vulnerability management a success.
Software engineering and cyber security risks are related
In 2022, our data showed that lower build quality of software is correlated with a higher relative risk of vulnerabilities.
Why?
In a nutshell, lower-quality software is harder to understand, modify, and test, increasing the potential for error significantly. Lack of quality in design, architecture, and process, can fundamentally increase the risk of future security vulnerabilities as well.
The bar chart below shows that 2-star build quality is correlated with a higher relative risk of vulnerabilities. The relative difference between 2-star and 4-star quality systems is a shocking 85%.
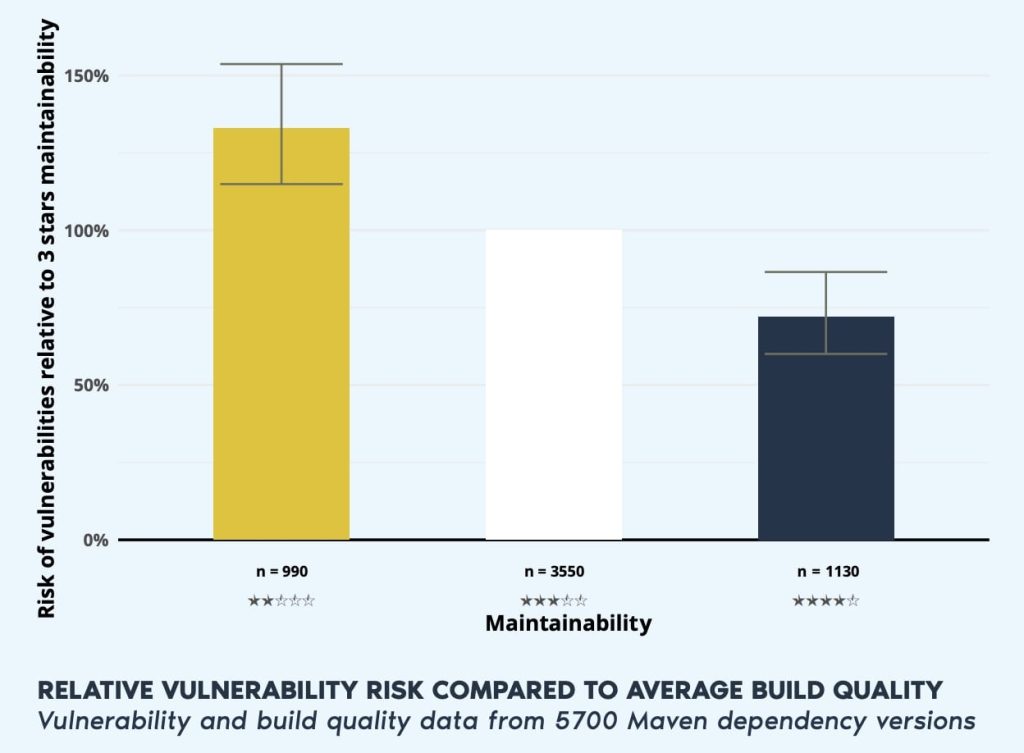
If you’re looking at the 4-star build-quality bar and noticing how systems of higher quality still pose significant risks, you’re not wrong. Vulnerabilities can occur at all levels of build quality and software is never perfect.
Additional tooling, secure software design, and process measures are required to further reduce security risks. But more on that later.
Software vulnerabilities, threats, and security risks explained
Before we dive into how software quality helps us mitigate security risks and enhances vulnerability management, it’s important to understand what threats, vulnerabilities, and security risks are in the first place. Let’s take a quick look at each of these terms in the context of software.
What are software vulnerabilities?
A vulnerability is a flaw or weakness in a software’s system, processes, design, implementation, or deployment. Vulnerabilities can be technical, like outdated dependencies, or human-generated such as design or coding errors.
Any of the following can lead to the exploitation of a vulnerability in the software:
- Outdated dependencies
- Lack of proper encryption standards
- Weak password requirements
- Human error (e.g. design or coding errors)

What is vulnerability management?
Vulnerability management is the continuous discovery, prioritization, and resolution of security vulnerabilities in an organization’s IT infrastructure and software.
What are software threats?
A threat is anything that could exploit a vulnerability and cause harm. The way how threats are exploited by hackers (or other threat actors), is called an attack vector. An attack vector is an umbrella term and refers to the method or pathway used to illegally access a computer or network to try and exploit system vulnerabilities.
Current cyber security threats
According to ENISA, the European Union Agency for Cybersecurity, 2023’s prime threats are:
- Ransomware
- Malware
- Social engineering
- Threats against data
- Threats against availability: Denial of Service or Internet threats
- Information manipulation and interference
- Supply chain attacks
Threat actors (such as hackers) may have different motivations for carrying out attacks, for example, financial gain, espionage, disruption, destruction, or ideological (such as hacktivism).
While cyber-attacks are intentional – like the complex cyberattack on the UK Electoral Commission in 2023 that exposed the data of 40 million voters, threats can also be unintentional, meaning they originate from a human error like the accidental disclosure of sensitive information.
What are software security risks?
Risk is the probability of a threat taking advantage of a vulnerability and causing harm. It refers to the potential loss or damage associated with a specific threat – like the $52 million loss from a cyberattack on MGM Resorts in 2023.
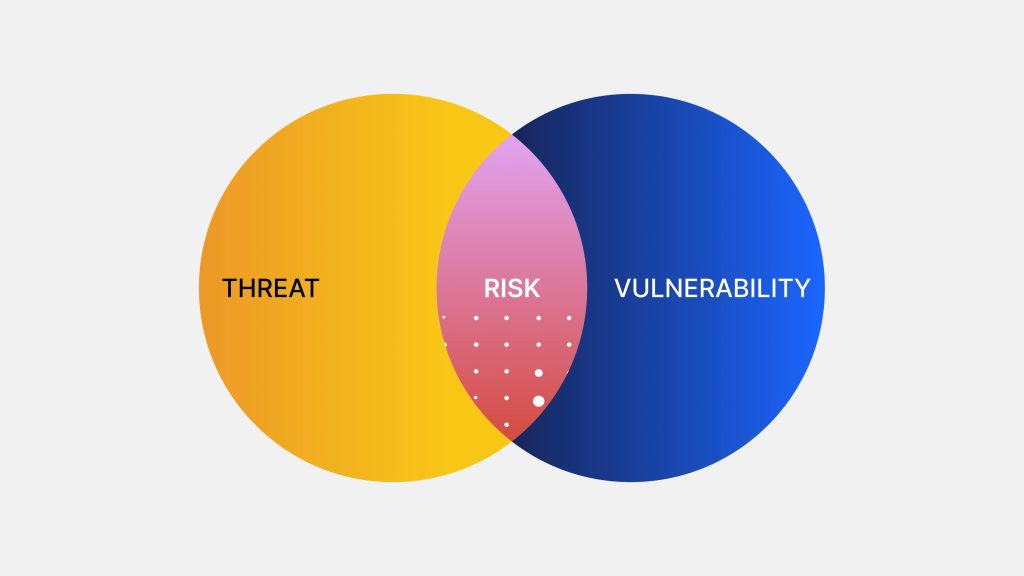
In the visual below, you can see how risk is the intersection of threats and vulnerabilities.
The more vulnerabilities you have, the more threats arise, leading to more risk for your organization.
Since external threats cannot be mitigated, it’s of utmost importance to reduce the number of vulnerabilities, or even better, prevent them from being created in the first place.
The role of software quality in mitigating software security risks
The problem with security risk is that no matter how advanced your systems are, it’s impossible to eliminate all vulnerabilities. However, better software quality will help you reduce the risks. Or, at least, help you identify vulnerabilities before they can be exploited.
This is where Software Quality Management (SQM) comes in: the continuous process of monitoring, controlling, and coordinating policies, procedures, activities, and people to achieve your software quality objectives – ultimately reducing security risk and vulnerabilities.

Enhancing cybersecurity through Software Quality Management (SQM)
The correlation between software quality and cybersecurity is undeniable. Lower-quality software often harbors vulnerabilities that can be exploited, leading to significant security breaches. With the average data breach costing organizations approximately $4.9 million (IBM), proactively improving software security has become crucial for business leaders.
Companies initiating a Software Portfolio Scan set themselves on a path toward achieving software that’s up to 2 times more secure, significantly reducing their cybersecurity risks. By embedding quality insights into their software management strategies, IT leaders can avoid costly breaches while fostering more secure, resilient software portfolios.
How software development best practices reduce security risks
When code adheres to software quality objectives, it becomes a lot easier to understand, modify, and test, leading to reduced risks and a more secure environment.
Let’s use a simplified analogy to clarify.
When cooking in an organized kitchen you can quickly locate your cooking utensils, and work with fresh ingredients (all clearly labeled with expiration dates). Now, if the environment you work in is clean as well, you further reduce the risk of serving your guests a plate filled with bacteria that weren’t part of the original recipe.
In a way, the same applies to developing software code. You can put something together quickly without paying attention to any quality objectives. The system you put together might work from a functional point of view, just like the plate of food from a dirty kitchen might still taste good.

However, because it’s not created according to software quality objectives, your code might be filled with vulnerability risks. Because you didn’t work in a “clean kitchen” it will be a lot harder to spot risks.
“Cooking in a dirty kitchen” puts your organization at risk, and not being able to spot those risks can lead to serious problems real fast.
While this article focuses on software security risk, there is a lot more to it. At Software Improvement Group we analyze risks of low software quality not just from a security point of view. We also consider the effect it has on time-to-market, higher costs, legal issues, and regulatory compliance, just to name a few. We’ll talk about those in more detail in other blog posts.
Start improving the quality of your software portfolio today.
The unfortunate reality is that 66% of organizations are planning to increase security investments as a result of a breach.
Why wait for a crisis to prioritize software quality? Start improving the quality of your software portfolio today. However, just looking for a vulnerability scanner or vulnerability management tools might not suit the needs of your multifaceted software portfolio.
At Software Improvement Group, we help organizations like yours improve the quality of their software portfolio, with our all-in-one software excellence platform, Sigrid. Find out more about how we provide unified risk-based and actionable insight into the security of your entire portfolio.